Main | Download | Documentation
Welcome to REMO
This is a project to build a graphical rule editor for ModSecurity with a positive/whitelist approach.
There is a beta release 0.2.0, but it’s better to work with the development sourcetree.
Basic Concept
ModSecurity is not a simple toy. It is quite tricky to configure successfully. Many web applications are not very simple either. Bringing them together by writing a tight ModSecurity ruleset is very difficult. Modsecurity.org advertises a tested core ruleset granting you protection from most known attacks. But this is only a blacklist approach: All known dangerous traffic is filtered out.
A network firewall uses a whitelist approach; also called positive security model: Everything is dropped outside of a short and strict rulset. An application firewall should do exactly the same. (See Ivan Ristic’s thougts on positive security. Ivan Ristic is the man behind ModSecurity.)
But this comes with a catch: Your application does not come with a short and strict ruleset and writing one will be tough. This is the point where remo comes into play. It is meant as a graphical editor for this ruleset, thus helping you to generate a whitelist of valid requests to your application. Ideally you will be able to bundle this ruleset with every release of your online application.
Features
This is the short list of features done so far:
* Ruby on rails application with ajax use
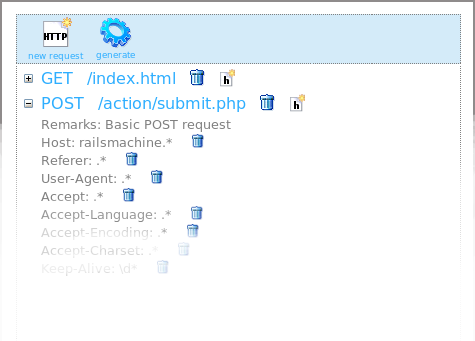
* Enter http requests, display them, edit them, delete them, rearrange them
* Edit the http headers of the requests
* Edit the query string parameters
* Edit the cookie parameters
* Edit the post payload arguments
* Every argument can be optional or mandatory
* The response to every argument failure can be configured specially including http status code and optional redirect location
* Argument names can contain regular expressions themselves
* Default value domains for all arguments. So you do not have to edit a regular expression for every parameter. Just select a predefined value.
* Generate positive ModSecurity2 ruleset
* Import ModSecurity audit-logs
* Check requests in the audit-log against the ruleset in development to find out wether it will work in practice
Future plans
Remo is currently on hold. That is it works, but I lack the time to continue development. The following is a list of features I have in mind:
* Authentication and session support in Remo
* Cover performance issues
* Proxy-mode for on the fly rule development
* New CSS with better looks
* Bring a decent look to Remo in Internet Explorer
* Better default value domains
* Polish the application
See the download section for the sourcecode and regression tests of the codebase. There is an online demo of the latest code, there are screenshots and even a video.
Your feedback and your feature requests are very welcome! Really.
You can contact me, the developer, via christian.folini at netnea.com.